Our connected world offers tremendous benefits for healthcare, but these advances come with risks. How do you navigate the complexities of “privacy and security navigating the challenges of connected health in a digital age”? We deliver tangible guidance to tackle the very real threat of data breaches and hacking in the world of connected health. Stay informed on the latest protections against these digital vulnerabilities without compromising the innovations meant to improve healthcare.
Key Takeaways
- The rapid integration of connected health devices and Electronic Health Records (EHRs) in healthcare has introduced significant cybersecurity risks, requiring stringent security practices and regulatory compliance to protect sensitive patient information.
- Regulatory compliance in connected health is complex, with multiple jurisdictions like the GDPR and CCPA imposing different requirements, making it crucial for healthcare organizations to develop comprehensive and flexible data privacy strategies.
- Security in connected health is not just about technology; it involves fostering a culture of security, implementing robust measures like data encryption and user authentication, and providing continuous training to mitigate human factors in cybersecurity breaches.
Connected Health and Data Security
The advent of connected medical devices and wearable technology in healthcare has transformed the way we monitor and manage health conditions. From remote patient monitoring tools to advanced fitness trackers, these mobile devices have become an integral part of modern healthcare. However, the proliferation of these devices also introduces cybersecurity risks as they capture, transmit, and store sensitive patient information.
Unfortunately, many of these medical devices were not initially designed with robust security, leaving them vulnerable to cyberattacks. Incidents of successful compromises of devices like insulin pumps and pacemakers have underscored the potential risks. Looking forward, healthcare organizations must stay alert. They need to collaborate and strike a balance between the progress in connected health technologies and the security and integrity of patient data – an initiative that isn’t just wise but crucial.
Navigating this new digital landscape can be daunting, but with the right security practices and measures, we can harness the power of connected health without compromising the privacy and security of patient data. Through a combination of technical security measures like data encryption and regulatory compliance, healthcare organizations can protect patient data from potential breaches.
Electronic Health Records
One of the cornerstones of the digital transformation in healthcare is the advent of Electronic Health Records (EHRs), also known as medical records. These digital records contain a wealth of sensitive patient information, from names and addresses to tests, diagnoses, and treatment histories. However, this wealth of data also makes EHRs a prime target for security breaches.
The majority of these security breaches are often caused by human error, such as falling for phishing scams rather than malicious intent. This underscores the need to adopt standards like IHE profiles in the public procurement of EHR systems to guarantee the secure exchange of health information.
In addition to implementing robust security systems, healthcare providers must also maintain transparency about their privacy policies and communicate clearly with patients. Addressing patient concerns about their EHR information’s privacy is vital for fostering trust and ensuring the effective use of these digital technologies.
Wearable Devices
Alongside EHRs, wearable digital health technology is playing an increasingly significant role in healthcare. Devices like fitness trackers and smartwatches allow for the monitoring of individual activity levels, heart rate, and sleep patterns, providing valuable data for both individuals and healthcare providers.
However, the rise of these devices also brings with it a host of privacy concerns. Unclear usage policies for data shared with third-party apps and services can lead to health data being sold or used without consent. Furthermore, the storage of personal health data collected by these devices in the cloud can grant access to various companies and researchers.
To lessen these privacy risks, entities such as wearable manufacturers must adhere to data privacy regulations. This includes establishing new data security processes to protect against potential security breaches if data is not adequately encrypted and protected.
Regulatory Compliance and Connected Health
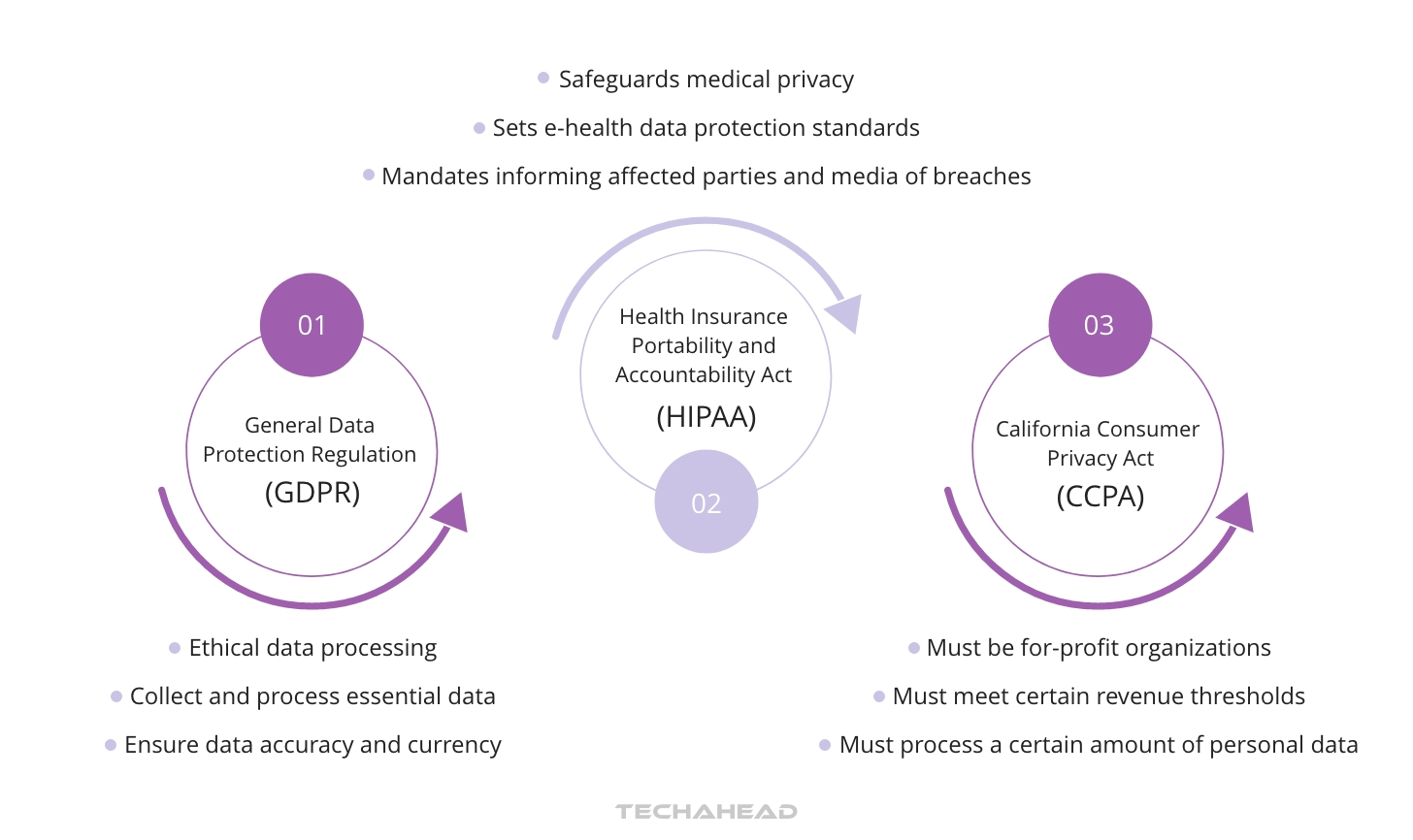
With the rise of connected health, regulatory compliance has become a vital part of ensuring the privacy and security of health information. Regulations like the General Data Protection Regulation (GDPR) impose strict rules on data privacy, including the ‘right to erasure.’ This means healthcare systems must manage data integrity carefully and ensure secure deletion.
In the U.S., the Health Insurance Portability and Accountability Act (HIPAA) provides federal protections for personal health information. There are strict requirements for security, privacy, and breach notification to safeguard electronic Protected Health Information (ePHI).
Despite these existing regulations, there remains a need for stronger regulations and industry self-regulation to enhance the protection of personal health data and maintain user autonomy. Undoubtedly, successfully navigating the intricate regulatory landscape plays a significant role in ensuring data privacy and security in connected health.
California Consumer Privacy Act
One important piece of legislation in this landscape is the California Consumer Privacy Act (CCPA). This Act applies to for-profit organizations in California, including healthcare providers, that meet specific criteria:
- They must be for-profit organizations
- They must operate in California
- They must meet certain revenue thresholds
- They must process a certain amount of personal data
The CCPA broadens data privacy protections within healthcare organizations to encompass all individuals, including clinicians and staff who were not covered under HIPAA. Furthermore, healthcare organizations with operations in California must extend CCPA’s data privacy measures universally within their company, ensuring that California residents receive the same privacy protections across states.
The enactment of the CCPA fosters a shift towards uniform data privacy protections beyond California, challenging the previous approach of adhering to different legal requirements state by state.
Navigating Multiple Jurisdictions
Navigating the regulatory landscape becomes even more complex when operating across multiple jurisdictions. With privacy laws existing in 12 states and more legislation pending, healthcare organizations face a daunting task.
The applicability of state privacy laws varies widely, with different thresholds and revenue-generation requirements determining an organization’s obligation to comply. This leads to a categorization of health-related information as sensitive data and variations in consent requirement or opt-out provisions amongst states.
To ensure compliance, healthcare organizations must align their privacy policies with state requirements, maintain specific contracts with vendors, and accommodate different effective dates of the laws. Developing both short-term and long-term, enterprise-wide strategies for regulatory compliance is vital due to the variations and impending changes in data protection laws across multiple jurisdictions.
Implementing Strong Security Measures
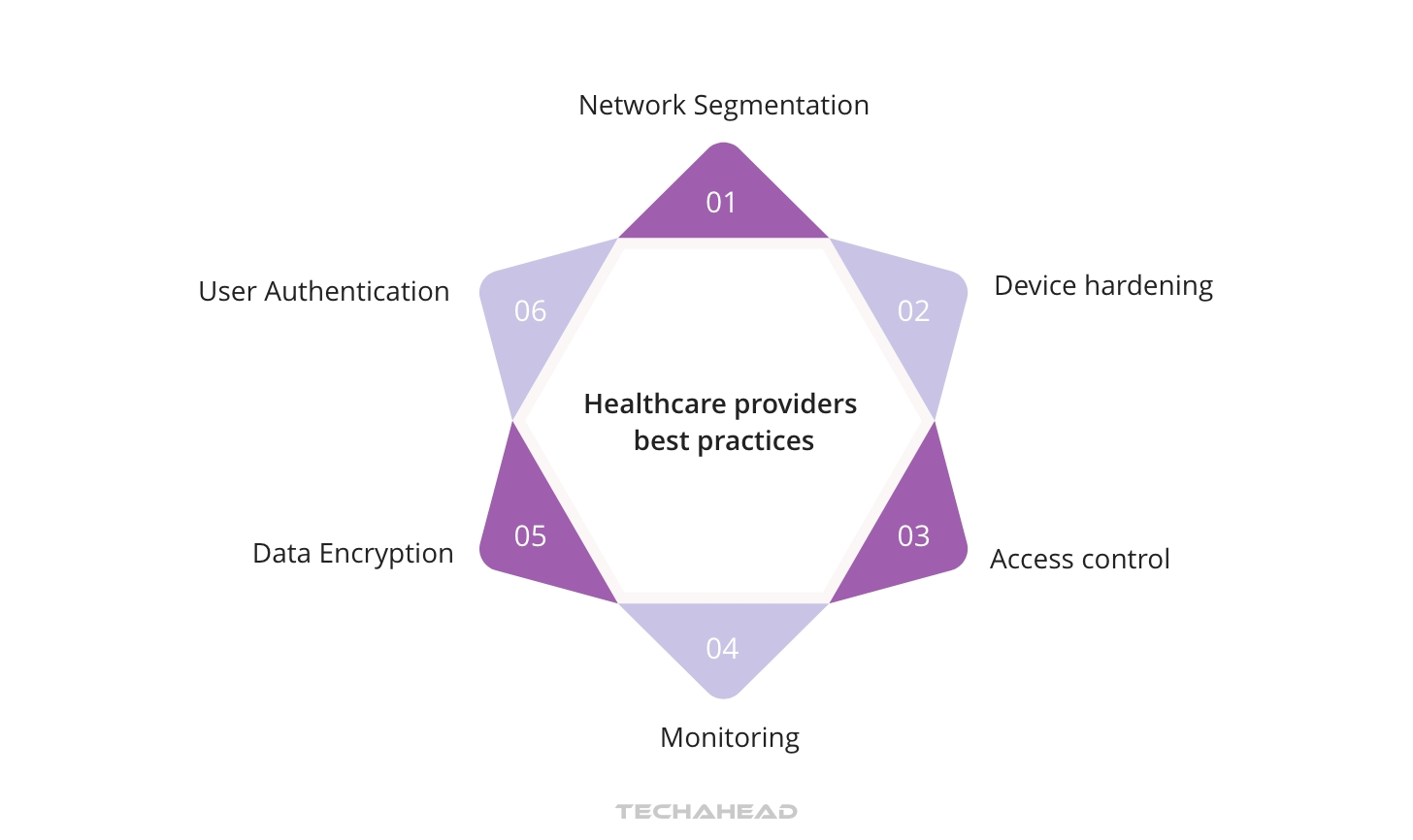
In addition to regulatory compliance, healthcare providers also have a responsibility to secure connected devices through best practices. This includes:
- Network segmentation
- Device hardening
- Access control
- Monitoring
It’s also vital to have an incident response plan in place to lessen the impact of security incidents.
Cybersecurity management requires collaboration with manufacturers and providers, particularly to secure older medical devices in accordance with FDA guidelines. This is crucial for:
- Protecting against threats that could harm patients or disrupt patient care
- Conducting risk assessments to identify device vulnerabilities and prioritize threats
- Preventing data breaches and protecting against identity theft.
Data breaches from healthcare devices can have significant repercussions, leading to the exposure of sensitive medical information and resulting in substantial financial impact and identity theft. In light of the increasing risk of a data breach, it is vital to implement robust security measures for protecting patient data and fostering trust in healthcare services.
Data Encryption
One key security measure in healthcare is data encryption. This process involves transforming data into an unreadable format, known as ciphertext, to prevent unauthorized access and ensure patient privacy.
To secure Electronic Health Records, strategies like maintaining backup systems, deploying firewalls, and utilizing encryption for data security during information exchange are employed. However, even encrypted patient data can be at risk from improper handling, such as emailing or pasting into documents, and the storage of decryption keys on easily accessible devices.
Therefore, it’s evident that data encryption isn’t solely about deploying the technology but also about setting up secure processes for managing and storing both the encrypted data and decryption keys.
User Authentication
Beyond encryption, authentication is another crucial aspect of securing patient data. Authentication verifies user identity and distinguishes what actions an authenticated user is allowed to perform. Establishing strong password policies and secure password management practices is vital to protect against unauthorized data access.
Two-factor Authentication (2FA) enhances security by requiring users to provide a second form of verification in addition to a password. Furthermore, the adoption of zero trust architecture, which incorporates continuous multifactor authentication, is particularly pertinent in healthcare settings where users may log in from various locations.
The Human Factor and Training in Connected Health
The human factor in connected health cannot be overlooked. Security breaches of electronic health records (EHRs) have a substantial financial impact on the U.S. healthcare industry, with an estimated annual cost of $6.5 billion. Despite efforts to comply with HIPAA regulations, security breaches continue to compromise patient health information, indicating a need for better training programs.
Education is a fundamental element in addressing privacy concerns. It empowers healthcare professionals and patients to make informed decisions and maintain the security of personal information. By creating awareness and promoting understanding of data privacy and security principles, we can ensure the safe use of digital technologies in healthcare.
Cybersecurity Training
Healthcare staff must be trained regularly to be aware of ransomware attacks, phishing scams, and other cybersecurity threats. Promoting vigilance in recognizing and responding to potential security incidents is crucial.
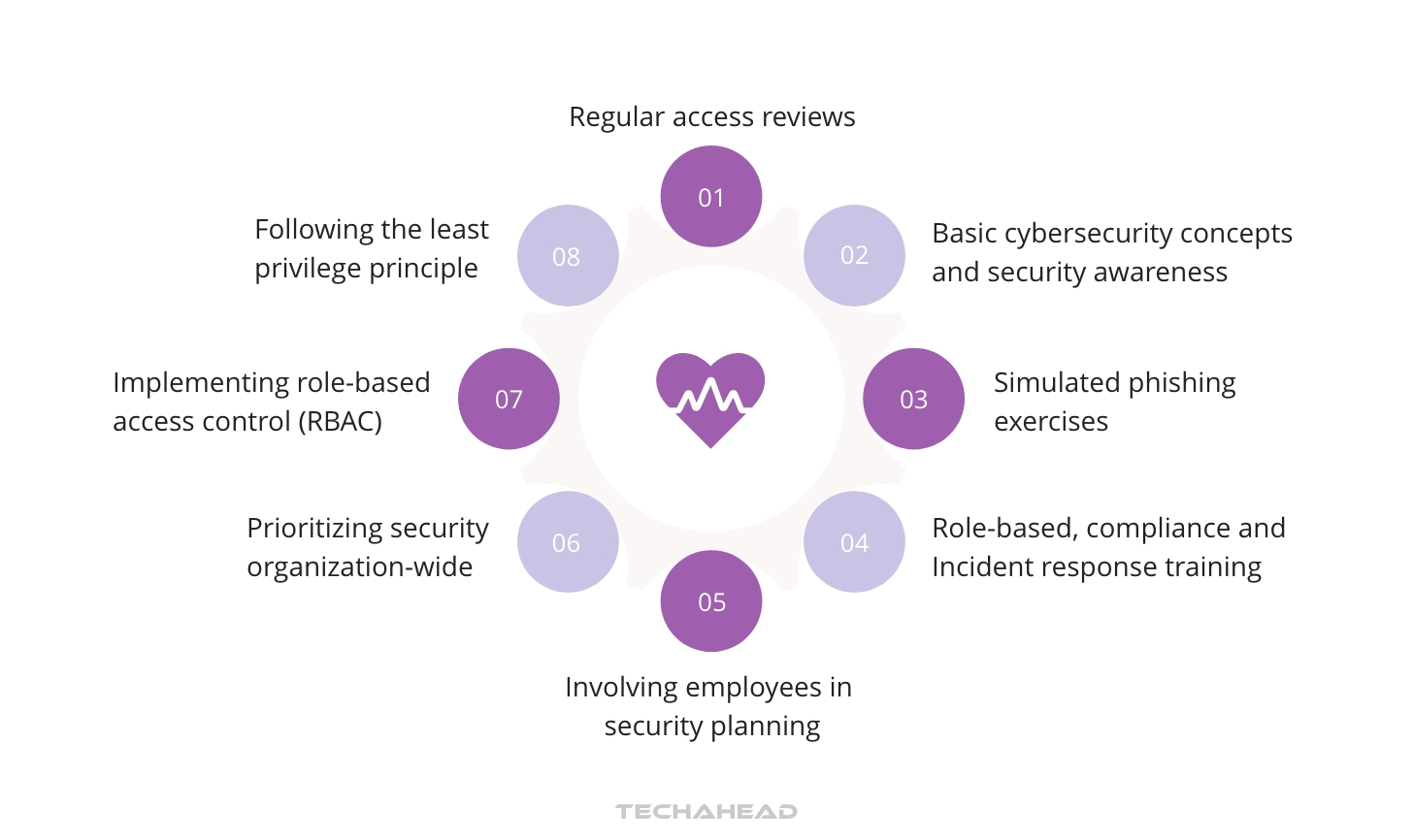
An effective cybersecurity training program should encompass:
- Basic cybersecurity concepts
- Security awareness
- Role-based training
- Compliance training
- Simulated phishing exercises
- Incident response training
Given the constantly changing threat environment, ongoing and routine cybersecurity training is necessary for healthcare staff.
Healthcare organizations are also recommended to conduct annual HIPAA cybersecurity training for employees and maintain documentation of this training as part of their incident response strategy.
Encouraging a Culture of Security
Beyond training, healthcare organizations can foster a security culture by:
- Involving employees in security planning and decision-making
- Giving priority to security throughout the organization
- Implementing role-based access control (RBAC)
- Adhering to the Principle of Least Privilege (PoLP)
- Conducting regular access reviews
These methods are crucial to ensure that user permissions remain appropriate and minimize unnecessary access to sensitive information.
Creating a culture that values security is essential for:
- Safeguarding personal information
- Maintaining the confidentiality and privacy of patient data
- Retaining trust in healthcare services
- Improving resilience against cyber threats
- Guaranteeing the ongoing safe use of digital technologies in healthcare
By cultivating a security culture, healthcare organizations can achieve these goals.
Future Trends in Data Privacy and Security
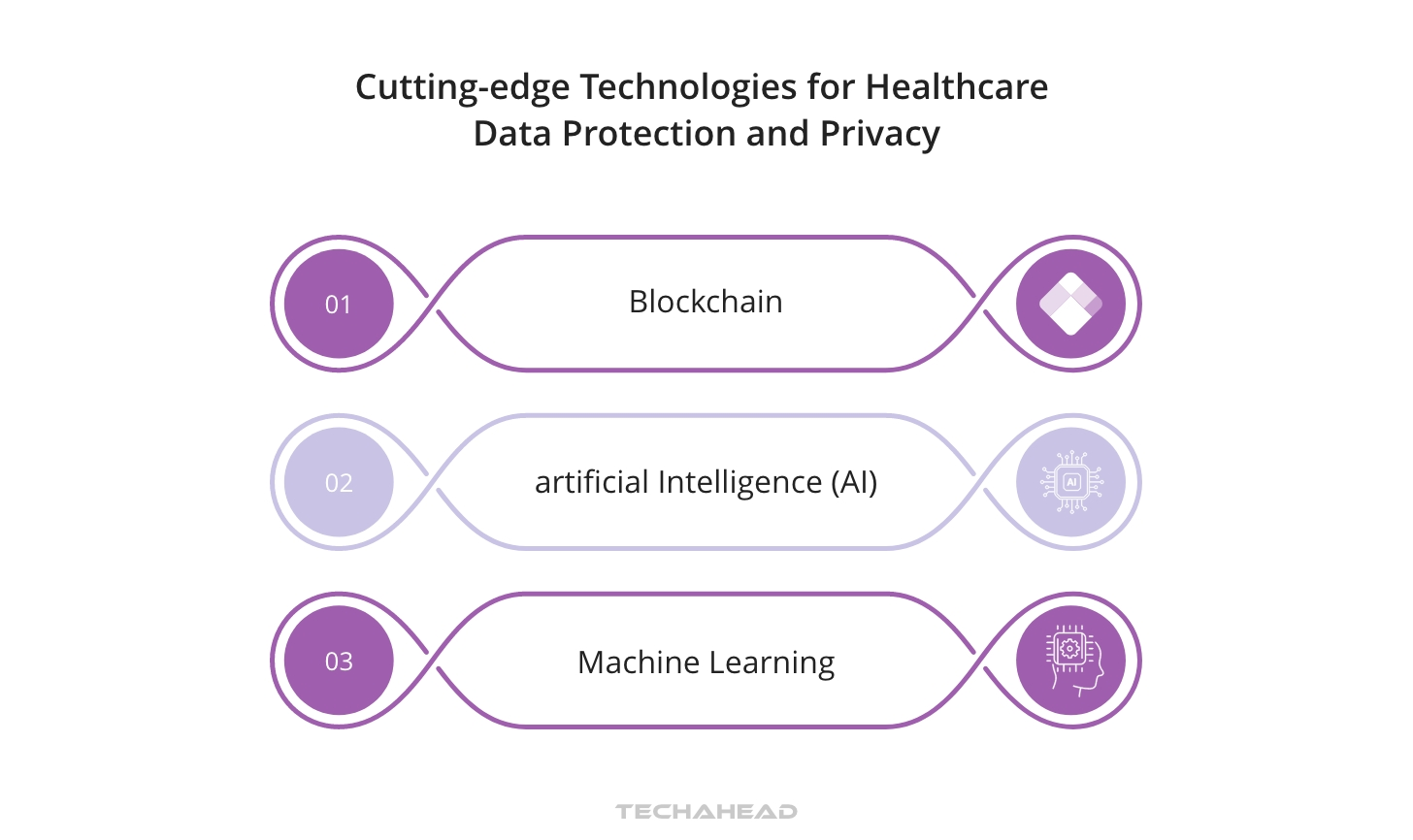
Looking forward, emerging technologies like blockchain, artificial intelligence (AI), and machine learning present both challenges and opportunities for data protection and privacy in healthcare. Blockchain technology, for instance, is being recognized for its potential to ensure data integrity and securely exchange health information in the healthcare sector.
Artificial intelligence and machine learning are key emerging trends in healthcare, supported by legislation such as the Executive Order on Safe, Secure, and Trustworthy Artificial Intelligence. This legislation emphasizes the importance of privacy and transparent reporting, underscoring the need for robust data privacy and security measures in the age of AI and machine learning.
However, advances in digital technologies also pose challenges for data protection. As these technologies continue to evolve, new approaches will be needed to manage one’s own personal data, cross-border data transfers, and user privacy.
Navigating these challenges and opportunities will play a crucial role in ensuring data privacy and security in the future of connected health.
Privacy-Preserving Technologies
As the volume of data grows, organizations are increasingly investing in advanced technologies for data collection and data generation, automatically discovering and protecting sensitive information. Techniques such as data minimization and anonymization are vital for ensuring the privacy of patient data in the face of escalating data volumes.
Decentralized security models, such as blockchain, secure multiparty computation, and homomorphic encryption, are emerging in response to these challenges. By distributing data across multiple servers, these models enhance security while maintaining functionality.
The emergence of these privacy-preserving technologies signifies a major milestone in the journey towards ensuring data privacy and security in connected health. By harnessing these technologies, healthcare organizations can proactively address the privacy concerns associated with escalating data volumes and increasingly sophisticated cyber threats.
Zero Trust Architecture
Another emerging trend in data privacy and security is the adoption of zero trust architecture. The National Institutes of Standards and Technology’s Special Publication 800-207 provides a framework and roadmap for zero-trust architecture, applicable to both public agencies and private healthcare organizations.
Zero trust architecture is built on five pillars:
- Identity
- Device
- Network/Environment
- Application Workload
- Data
Zero trust architecture, which incorporates continuous multi-factor authentication, bolsters security, especially in healthcare settings where users may login from different locations.
The adoption of zero trust architecture represents a paradigm shift in data security. By embracing this approach, healthcare organizations can enhance their security posture, reduce the risk of data breaches, and further ensure the privacy and security of patient data.
Summary
Navigating the intersection of technology and healthcare is no small feat. The advent of connected health brings with it a host of opportunities and challenges, with data privacy and security standing at the forefront. From implementing robust security measures to ensuring regulatory compliance and fostering a culture of security, healthcare organizations are tasked with protecting sensitive patient data in an increasingly digital world.
However, the journey doesn’t end here. With emerging technologies like blockchain, AI, and machine learning, the landscape of data privacy and security in healthcare is continuously evolving. As we look to the future, it’s clear that the journey towards ensuring data privacy and security in connected health will involve continuous learning, adaptation, and innovation.
Frequently Asked Questions
Why is security and privacy important in the digital age?
In the digital age, security and privacy are crucial because they protect sensitive personal information and guard against identity theft and cybercrimes. It is important to prioritize these aspects to maintain personal autonomy and security.
What are the biggest challenges in digital health?
The biggest challenges in digital health include data security, privacy concerns, ease of use, scalability, evolving patient needs, and the role of AI. Additionally, lack of evidence-based standards, data governance issues, and ethical concerns impede the progress of digital health (12, 14). Privacy concerns are particularly heightened due to the sensitivity of health data when digitized (14).
Why is privacy and security important in health care?
Privacy and security are important in health care to ensure that patients have control over their health information and to protect them from potential harm and breaches of confidentiality. It also promotes effective communication between providers and patients.
Why is regulatory compliance important in ensuring data privacy and security in connected health?
Regulatory compliance with data privacy laws like GDPR and HIPAA is crucial for protecting patient health information, as these laws impose strict rules on data privacy and require healthcare organizations to have systems in place for security, privacy, and breach notification.
How can healthcare organizations develop a culture of security?
To develop a culture of security, healthcare organizations should involve employees in security planning, prioritize security across the organization, implement role-based access control, and provide regular training and education on data privacy and security principles. This creates awareness and understanding, fostering a culture of security within the organization.