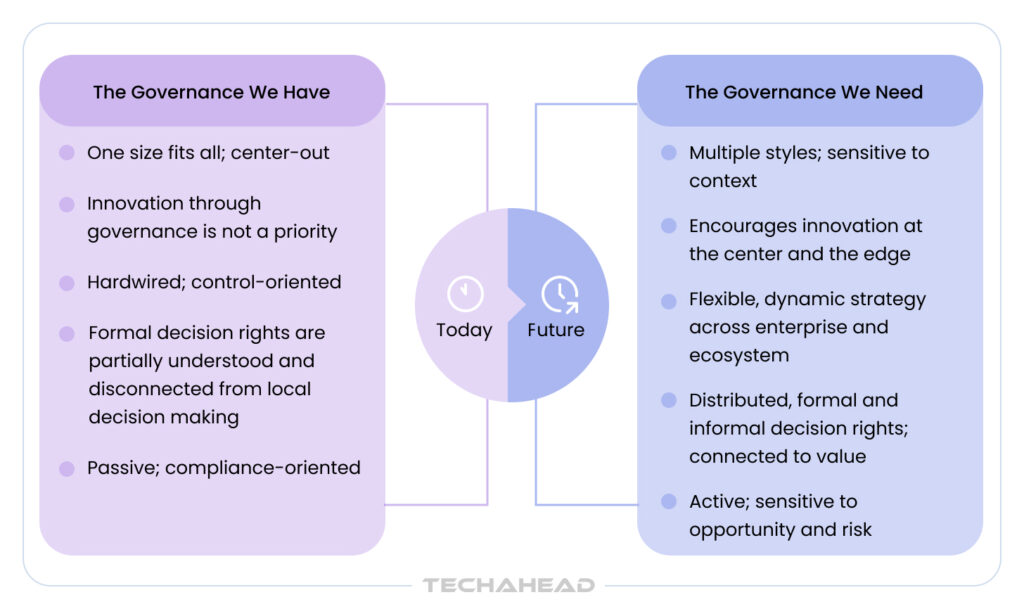
The AI deployment playbook has fundamentally changed from what it used to be. What worked for traditional software rollouts – “build, test, deploy, monitor”, breaks down when you’re dealing with systems that learn, adapt, and make decisions with incomplete visibility into how they reached those conclusions. Organizations that recognize this distinction early are building sustainable AI programs. Those that don’t are accumulating technical debt that compounds with every new model pushed to production.
Here’s the gap most enterprises haven’t addressed:
According to Gartner, by 2027, 80% of data and analytics governance initiatives will fail due to a lack of focus on tangible business outcomes. These aren’t negligent organizations. They’re enterprises with mature IT infrastructure, compliance frameworks, and substantial security investments.
Suppose your company launched governance programs, drafted policies, and formed committees. Yet when regulators ask “show us the lineage of this decision,” or auditors demand “prove this model wasn’t trained on poisoned data,” those governance initiatives fail to deliver answers.
Key Takeaways
- 80% of AI governance initiatives fail due to platforms lacking in “provenance”, “traceability”, and “enforcement architecture”
- Effective platforms tend to reconstruct complete decision paths, analyze impacts, and quantify AI risks continuously
- Provenance requires automatic lineage capture, traceability needs cross-platform correlation, governance demands pipeline-integrated enforcement mechanisms
- Platform evaluation should focus on architectural fit and integration requirements, not vendor demos or feature checklists
- Successful implementation requires custom development, specialized engineering talent, and ongoing operational capacity beyond platform licensing costs
The question isn’t whether your organization will face scrutiny. It’s whether your governance initiative will be among the 20% that actually works.

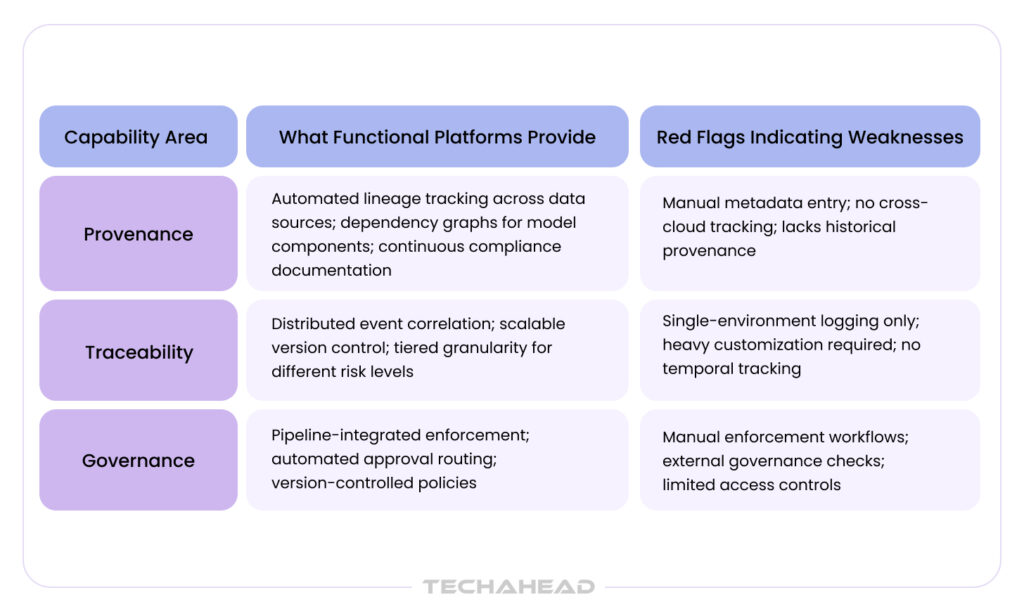
The Three Capabilities That Separate Functional Platforms from Shelf-Ware
When evaluating AI security platforms, most enterprises focus on feature checklists. But surface-level questions miss what actually determines whether a platform will work in production. Platforms that succeed deliver three foundational capabilities:
Complete Decision Path Reconstruction
When your machine learning model denies a loan application or flags a transaction as fraudulent, regulators want documented proof showing which datasets influenced the decision, what preprocessing occurred, who validated the model, and when the last bias audit happened.
What to look for in platforms:
- End-to-end decision traceability from raw data through preprocessing, training, validation, deployment, and individual inference
- Automated forensic reconstruction capabilities that can replay model decisions with full context
- Temporal consistency showing model state at any point in time, not just current state
Most enterprises discover too late that platforms offering “lineage tracking” only capture high-level metadata, not the granular decision paths regulators demand.
Must Read: Data Analytics for Fraud Detection and Prevention
Comprehensive Impact Analysis
Researchers at Carnegie Mellon’s CyLab demonstrated that manipulating as little as 0.1% of a model’s pre-training dataset is sufficient to launch effective data poisoning attacks. When training data is compromised, can you instantly identify every affected model across your infrastructure?
Critical platform capabilities:
- Bi-directional lineage showing both upstream data sources and downstream model dependencies
- Supply chain visibility for third-party models, pre-trained components, and fine-tuning datasets
- Impact analysis that instantly identifies all affected models when a data source is compromised
- Version correlation linking specific data versions to specific model versions across your infrastructure
The challenge compounds when you’re working with fine-tuned third-party models, open-source components, and proprietary datasets flowing through different teams. Platforms that can’t map these complex dependencies leave you blind during incidents.
Continuous Risk Quantification
Your board asks about AI risk exposure or Shadow AI with the same precision as financial risk. Can your platform deliver?
Essential capabilities to evaluate:
- Real-time model inventory across all environments; production, staging, development, shadow deployments
- Risk scoring and prioritization based on data sensitivity, use case criticality, and compliance requirements
- Drift detection and alerting when models deviate from validated behavior
- Compliance gap analysis showing where deployed models fail to meet regulatory requirements
- Executive dashboards translating technical metrics into business risk quantification
Recommended Read: Pillars of AI Security
The gap between “we have AI governance” and “we can demonstrate AI governance” is where enterprises get exposed. Platforms bridging this gap provide instrumentation, not just documentation.
Does your current platform answer these three questions, or does it just generate compliance reports nobody can act on?
Core Platform Architecture: What Actually Makes Governance Work
Understanding what to look for requires understanding why most platforms fail. The challenge isn’t features; it’s architectural foundations that enable those features to work at enterprise scale.
Provenance Architecture: Beyond Simple Metadata
Model provenance isn’t about maintaining a metadata field that says “trained on public dataset X.” It’s about creating an immutable chain of custody for every component that influences your AI’s behavior.
Effective provenance architecture addresses three fundamental requirements. Your training data doesn’t come from one clean repository. It’s aggregated from data lakes, third-party vendors, web scraping operations, purchased datasets, and real-time streaming sources. This is where most platforms reveal their limitations.
Related: Understanding Microservices (Architecture & Benefits)
What sophisticated provenance architecture delivers:
- Automated multi-source lineage capture: Platforms that work in production environments integrate directly with your data catalogs, warehouses, and lakes to capture provenance continuously without human intervention. You shouldn’t be manually entering metadata fields. The platform should automatically track data flows as they happen across your infrastructure.
- Component-level dependency mapping: Modern AI relies on complex chains involving pre-trained models, transfer learning, fine-tuning datasets, and ensemble architectures. When vulnerabilities emerge in base models, you need platforms that instantly identify all downstream fine-tuned variants and production deployments affected. This requires graph-based relationship tracking, not just hierarchical version trees.
- Compliance-ready documentation generation: Regulations like the EU AI Act demand specific documentation about dataset characteristics, demographic representation, and consent mechanisms. Platforms architected for regulatory compliance maintain this documentation continuously as models evolve, not as audit-time reconstruction efforts. You want compliance documentation as a byproduct of normal platform operation.
Must Read: Strategies for Gen AI and LLM Security
Architectural weaknesses that signal problems
Platforms requiring manual metadata entry lack integration depth for enterprise scale. If systems can’t trace lineage across cloud environments or organizational boundaries, they reveal architectural limitations. Watch for platforms providing only current-state lineage without historical provenance. Solutions lacking integration with your specific data infrastructure will require substantial custom development you’ll need to budget for.
Must Read: How AI Augmentation Empowers Modern Enterprises
Traceability Architecture: Coherent Audit Trails Across Distributed Systems
Traceability sounds straightforward until you’re operating AI at scale across hybrid cloud environments. The real challenge? Creating coherent audit trails when your model lifecycle spans Kubernetes clusters, serverless functions, edge devices, and SaaS platforms.
Your models train in SageMaker, orchestrate through Databricks, deploy to Kubernetes, serve predictions via cloud provider services, and log results to on-premise systems. This distributed reality is where traceability architecture either works or breaks down.
Critical traceability capabilities you need:
- Cross-platform event correlation: Platforms with enterprise-grade traceability architecture don’t just collect logs. They build intelligent correlation layers that reconstruct complete workflows across disparate systems using distributed tracing frameworks, event normalization capabilities, and temporal correlation algorithms that function across technology boundaries.
- Enterprise-scale version control: When managing hundreds or thousands of models across development, staging, and production environments, you need platforms that maintain complete version histories. This means tracking which model version runs in each environment, who authorized each deployment, what approval workflows were satisfied, and what configuration parameters were active. Graph database capabilities become essential for tracking relationships between model versions, deployment targets, approval chains, and runtime configurations simultaneously.
Red flags indicating architectural limitations
If platforms only capture events within their native environment, they can’t provide enterprise-wide traceability. Solutions requiring extensive custom development for deployment infrastructure integration reveal architectural inflexibility. Systems unable to correlate events across different cloud providers demonstrate distributed systems architecture gaps. Platforms providing only current-state visibility lack the temporal data architecture you’ll eventually need.
Governance Architecture: Integration That Enables Enforcement
Here’s where most AI governance initiatives fail. It’s not because of policy gaps. It’s because platforms can’t integrate with actual development workflows. You can have comprehensive policies documented beautifully, but if they exist as PDF documents rather than enforced constraints, they accomplish nothing.
Effective governance requires architectural capabilities that transform policies from documentation into automated enforcement mechanisms.
Development pipeline integration that actually works
Governance needs to operate within development workflows, not alongside them. Look for platforms providing native plugins for Jenkins, GitLab, GitHub Actions, and Azure DevOps that enforce governance rules as code gates in deployment pipelines. The architectural distinction is critical: governance checks should be automated pipeline stages that block non-compliant deployments, not manual review steps developers can bypass. Platforms with robust cloud governance architecture make it structurally impossible to deploy non-compliant models, not just difficult.
Multi-stakeholder workflow orchestration
Your governance involves data scientists, ML engineers, security teams, legal counsel, and compliance officers. Each needs appropriate access, approval authority, and visibility. Sophisticated platforms automatically route high-risk deployments through approval chains based on configurable rules. You define thresholds for what triggers legal review, what requires security sign-off, and what needs compliance validation. The platform enforces these workflows programmatically.
Policy-as-code enforcement capabilities
Can you define governance rules programmatically rather than through UI configuration? When regulations change, you need to update policies once and have them propagate to all deployed models automatically. The best platforms treat policies as living code that evolves with regulatory requirements. This means version-controlled policy repositories, automated policy testing, and rollback capabilities when policy changes create issues.
Governance architecture failures to watch for
Platforms requiring extensive manual processes for policy enforcement won’t scale. If governance checks happen outside your development pipelines, developers will find workarounds. Solutions lacking role-based access control granularity create bottlenecks. Platforms where policy updates require configuration changes across multiple systems rather than centralized updates reveal architectural design problems you’ll struggle with long-term.
The Platform Evaluation Framework
Most platform evaluations focus on what vendors claim their products can do. The questions that actually matter focus on how platforms accomplish those claims in your specific environment.
The Questions Vendors Hope You Won’t Ask
These questions separate platforms that work in production from those that look good in demos:
- What percentage of customers required significant custom development to reach production?
- Can you provide reference architectures for organizations with our complexity level?
- What’s the typical implementation timeline for enterprises with multi-cloud, hybrid deployments?
- Who owns and maintains the custom code required for our specific integrations?
- What happens when we need to extend the platform for use cases you haven’t anticipated?

When Platforms Need Custom Development
Here’s what platform vendors won’t tell you: selecting a platform is the easy part. Making it work in your specific environment is where most organizations underestimate effort and cost.
What platforms actually provide:
- Core capabilities around model registry, basic lineage tracking, and policy management
- Standard integrations with popular tools like SageMaker, Databricks, common ML frameworks
- Foundational security and compliance features
- A starting point that still requires substantial engineering work to operationalize
What platforms don’t provide:
- Custom-built integrations for your proprietary systems and unique infrastructure
- Business logic engineered to match your specific governance requirements
- Operational systems architected around your organizational structure
- The development capacity to build everything that makes it work together at scale
- Ongoing engineering as your needs evolve
When Custom Development Becomes Essential
Even the best platforms require development work for production deployment:
Integration layers: Building connectors to proprietary systems, legacy infrastructure, or unique data sources the platform doesn’t support natively. Each integration point requires software development; APIs to be built, middleware to be engineered, data pipelines to be constructed, and monitoring systems to be coded.
Workflow customization: Adapting approval processes, stakeholder coordination, and escalation paths to your organizational structure. Platform templates rarely match the complexity of real organizational workflows.
Policy logic: Encoding your specific governance rules, risk frameworks, and compliance requirements beyond what platform templates provide. Industry-specific regulations often require custom policy validators.
Performance optimization: Tuning queries, storage, and processing for your specific scale and usage patterns. Platforms optimized for general use may require architectural work to handle your volume.
Reporting and dashboards: Creating executive views, compliance reports, and operational metrics tailored to your stakeholder needs beyond standard platform dashboards.
What Successful Implementation Requires
Organizations succeed when they approach platform selection as an engineering initiative:
Architecture-first approach: Start by mapping your complete AI ecosystem; data sources, ML frameworks, deployment targets, monitoring systems, compliance tools. This assessment reveals integration requirements early, enabling realistic scoping of custom development, testing phases, and maintenance protocols.
Specialized engineering talent: While worldwide AI spending is forecast to total nearly $1.5 trillion in 2025, finding teams that can actually build comprehensive AI security systems remains the bottleneck. You need developers with rare skill combinations: cloud-native architecture, MLOps pipeline development, security engineering, compliance automation, and domain expertise.
Operational sustainability: Post-deployment sustainability requires engineered solutions, not manual processes. Build automated systems for provenance tracking, custom dashboards for audit trail analysis, policy engines that enforce governance rules programmatically, alert systems with intelligent routing, and self-maintaining platforms.
Development capabilities you need:
- Software architects who translate business requirements into system designs across cloud, security, ML, and data engineering layers
- Engineering teams with proven experience building enterprise-scale AI security systems, not just implementing vendor platforms
- Developers who code compliance requirements directly into system logic spanning jurisdictions
- Full-stack development capacity to build integrations, extensions, APIs, and custom workflows platforms don’t provide
- Ongoing engineering resources who evolve the codebase as AI programs mature
Making the Decision: From Evaluation to Production
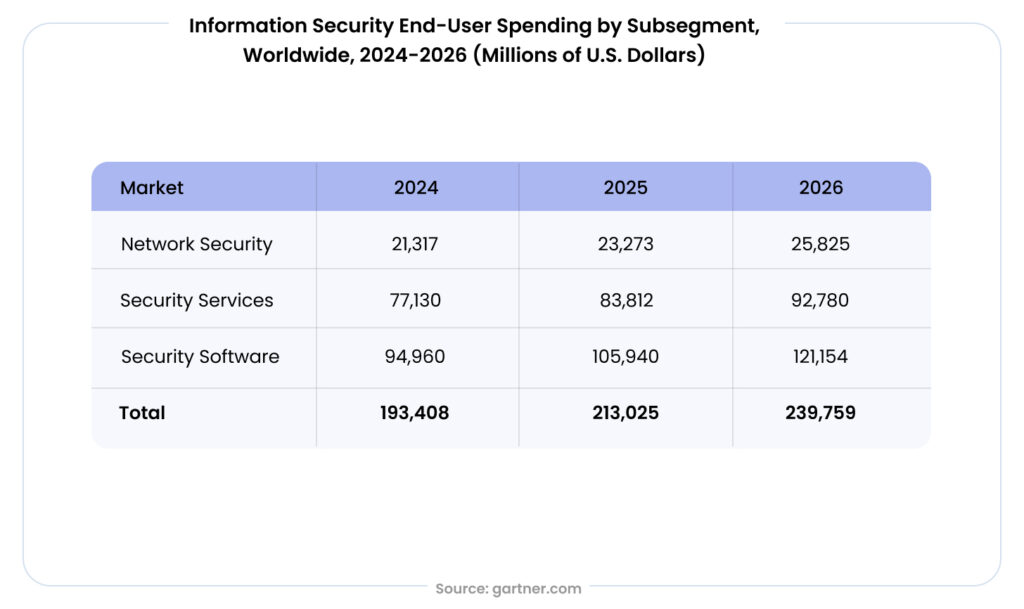
The enterprise AI security landscape is evolving rapidly. Global spending on information security reached $213 billion in 2025, driven by rising threats and expanding AI usage. Gartner predicts that by 2030, more than 40% of enterprises will experience security or compliance incidents linked to unauthorized shadow AI.
Organizations investing in comprehensive AI security platforms today position themselves to navigate increasing regulatory scrutiny. But platform selection is only the beginning.
Success Requirements
Architectural clarity: Understanding exactly how the platform will integrate with your specific infrastructure and what custom development that requires. Organizations that skip architecture planning consistently underestimate implementation effort by 300-500%.
Realistic planning: Budgeting for true total cost including implementation, ongoing operations, and platform evolution, not just licensing. Expect 2-5x platform licensing costs in implementation and customization.
Engineering capacity: Securing development expertise to build integrations, customizations, and operational automation that makes platforms work in practice. This isn’t optional, it’s essential for production success.
Operational commitment: Assigning ownership, establishing processes, and allocating resources for sustained platform operation and continuous improvement. Platforms fail when organizations don’t plan for ongoing operations.
The Platform Decision Framework
Phase 1: Requirements Definition Map all AI models across environments, document your complete ML technology stack, list applicable compliance frameworks with specific technical requirements, identify all stakeholders in AI governance, and prioritize models by risk level.
Phase 2: Platform Evaluation Use the evaluation framework to assess architectural fit, integration requirements, and reference validation. Eliminate platforms requiring extensive custom development in areas that should be standard.
Phase 3: Architecture Planning Design integration architecture, estimate development effort realistically, identify who will do implementation work, create deployment timeline accounting for complexity, and plan risk mitigation strategies.
Phase 4: Implementation Start with architecture design, phase rollout strategically beginning with highest-risk models, build for operational sustainability with clear ownership and automated processes, and plan for continuous evolution.
Measuring Success
Define metrics before deployment:
Technical metrics: Coverage of production models with complete provenance, query performance for compliance investigations, integration health and reliability, policy compliance rates
Operational metrics: Time to compliant production deployment, audit preparation efficiency, stakeholder satisfaction, reduction in governance violations
Business metrics: Deployment velocity, regulatory readiness, risk quantification capability, competitive advantage through mature governance
The organizations thriving in the AI era choose platforms with architectural alignment to their specific infrastructure, honestly assess and plan for required custom development, engage engineering expertise to bridge platform capabilities and operational needs, and treat platform deployment as an ongoing engineering initiative.
Ready to Evaluate AI Security Platforms With Architectural Clarity?
Platform selection decisions are too important to base on vendor demos and feature checklists. You need to understand what it will actually take to make any platform work in your environment.
Stop evaluating platforms in isolation. Start with architectural assessment that reveals what you actually need and what any platform will require to deliver it.
What successful platform evaluation requires:
- Current state architecture mapping of your AI infrastructure, data flows, and governance gaps
- Platform evaluation framework specific to your technology stack, scale, and regulatory requirements
- Integration architecture design showing exactly what custom development any platform will require
- Development effort estimation based on real implementation experience
- Total cost modeling revealing true investment beyond licensing fees
Don’t commit to a platform before understanding what it will actually take to make it work in your environment.
Conclusion
TechAhead, a global leader in AI-powered custom software development and cloud engineering, brings 16+ years of proven experience in architecting secure, scalable enterprise platforms. Ranked #1 globally in Clutch’s Spring 2025 App Development Awards and trusted by Fortune 500 brands including Audi, American Express, AXA, etc, we’ve delivered 2,500+ successful AI and cloud deployments worldwide.
Our AI security credentials:
- ISO 42001 certified and SOC 2 Type II compliant, meeting the latest international security standards
- AWS Advanced Tier Services Partner with dual competencies in AWS Security Services (across 8 security domains including AI Security, Threat Detection, and Data Protection) and AWS Cloud Operations (spanning 5 critical domains)
- Recognized by Webby Awards, Clutch, and Red Herring Global for innovation excellence
- Great Place to Work certified with 240+ expert developers specializing in AI/ML development, cloud architecture, and enterprise security
We don’t just implement platforms. We engineer custom AI security infrastructure from the ground up, integrating provenance tracking, governance automation, and compliance frameworks into your specific technology stack.
Ready to build defensible AI security architecture with a partner who understands both development and deployment reality?

Traditional data governance tools focus on structured data management, cataloging, and compliance for static datasets. AI governance platforms address dynamic challenges like model provenance, training data lineage, inference traceability, and ML pipeline monitoring. They track model versions, detect drift, manage model registries, enforce deployment policies, and provide audit trails for AI decision-making. Enterprise AI security requires platforms that understand machine learning lifecycles, not just data storage and access controls.
Implementation timelines vary based on infrastructure complexity, but enterprises should plan 6-8 months for production deployment. This includes architecture design (weeks 1-8), platform integration with existing MLOps tools and cloud environments (weeks 9-16), governance activation and policy configuration (weeks 17-24), and operational scaling. Organizations with multi-cloud deployments, proprietary ML frameworks, or complex compliance requirements often need additional custom development time. Realistic planning accounts for integration testing, stakeholder training, and phased rollout across business units.
Quality platforms provide native integrations with popular tools like SageMaker, Databricks, Kubernetes, MLflow, and major cloud providers. However, enterprises typically require custom connectors for proprietary systems, legacy infrastructure, and unique data sources. Evaluate platforms based on API extensibility, webhook support, and SDK availability. Ask vendors for reference implementations matching your specific technology stack. Most production deployments require software development to bridge platform capabilities with organizational workflows, approval processes, and compliance automation needs.
Organizations with mature AI governance achieve measurably better outcomes. Research shows AI-mature enterprises gain approximately 24% higher revenue growth compared to less-governed peers. ROI comes from accelerated model deployment velocity, reduced compliance violations and associated penalties, minimized security incidents from data poisoning or model manipulation, faster audit preparation, and improved stakeholder confidence. Quantifiable benefits include decreased time-to-production for compliant models, lower operational overhead through automation, and competitive advantage through demonstrated regulatory readiness and trustworthy AI practices.
Yes. While platforms provide foundational capabilities, ongoing success requires dedicated engineering capacity. Organizations need developers to maintain custom integrations as infrastructure evolves, update policy logic for changing regulations, optimize performance for growing model volumes, build specialized dashboards and reporting tools, and extend platform functionality for emerging use cases. Budget for full-time engineering resources covering cloud architecture, MLOps pipeline development, security automation, and compliance engineering. Platforms don’t eliminate maintenance needs; they provide frameworks requiring continuous development and operational support.




